I had coffee recently with a super fun group of ladies. The topic came up about personal information available on the internet when one mentioned she’d received an email from Facebook asking for her phone number. She ID’d it as a scam and deleted it. I believe it was probably a legit email, but it never hurts to be careful.
That discussion, and a request from a dear friend, warranted a blog about securing your online persona (a.k.a. choosing what people can see about you on the internet).
There are a lo t of articles dedicated to getting off the grid or becoming invisible on the internet. We’re not interested in going that far. People can know we’re on the internet, but if you’re like me, you want to control how much personal information leaks out. Me? I like to keep my public personal information to a minimum. My friends and family know how to contact me and that’s what’s important.
t of articles dedicated to getting off the grid or becoming invisible on the internet. We’re not interested in going that far. People can know we’re on the internet, but if you’re like me, you want to control how much personal information leaks out. Me? I like to keep my public personal information to a minimum. My friends and family know how to contact me and that’s what’s important.
In case you were wondering, here’s why websites ask for our phone numbers.
Reason One: New website security these days includes what they call “two-step” verification. Step 1: you log in with your normal user ID and password, Step 2: a security program sends a code to your phone via text, voice, or mobile app. You enter the newly sent code to log on.
Do you have to do this every time? No. There is a box to check or a question telling the security program to stop flagging the computer where you just logged on and to allow logging on from that computer without the code in the future.
Reason Two: Websites, such as Twitter, are allowing log ins with only a telephone number. There’s no user ID or password. You get a security code texted to that phone number and use it to enter the website.
 Reason Three: The website is using marketing apps. Advertising texts, including coupons, and voice mail marketing are part of this.
Reason Three: The website is using marketing apps. Advertising texts, including coupons, and voice mail marketing are part of this.
Reason Four: Websites where you transact business will ask for your phone number as well as your address. These websites usually have your info on a secure page (denoted by https:// at the beginning of the URL address).
Bank, broker, auction, and other financial or sales websites are different than social media websites like Facebook or Twitter. I don’t put my phone number on social websites; I don’t want to be that social. Facebook would like to be the next Amazon, and does offer advertising packages. But for the majority of Facebook users it’s still just another social media site. No hate mail please, Facebook lovers.
Whether you give out your phone number or not is up to you. I do on financial and sales sites because I want them knowing they can call me if there’s a problem. On social media sites, I do not. They have my email address; they can email me.
There is also the fact that typing my landline number into any search engine (Internet Explorer, Firefox, Chrome, etc) will pull up my address. If you know my cell phone number, my name and address can be requested for a fee.
Securing Your Online Information
Let’s talk about securing what personal information is floating out in cyberspace. The one we’ll tackle today is social media.
 We all love social media. There are so many wonderful things about it. It keeps us in touch with distant friends and relatives, and lets us know in real time what’s happening in people’s lives. We can view photos of loved ones we don’t see regularly, and follow businesses and events.
We all love social media. There are so many wonderful things about it. It keeps us in touch with distant friends and relatives, and lets us know in real time what’s happening in people’s lives. We can view photos of loved ones we don’t see regularly, and follow businesses and events.
In my opinion, the best of all worlds is to be able to utilize social media while keeping my personal information safe.
I’ve included a few the largest social media sites in the U.S. below. Believe it or not, there are dozens of others in almost every country around the planet. If your favorite isn’t listed, I bet you’ll see a trend in the below examples and be able to find your way through your site.
Facebook Privacy
Not long ago, Facebook redesigned its site to make it very easy to tighten up your personal information and security.
Find the padlock in the top right corner of your Facebook page. 1) Left-click on padlock, and select 2) Privacy Checkup.
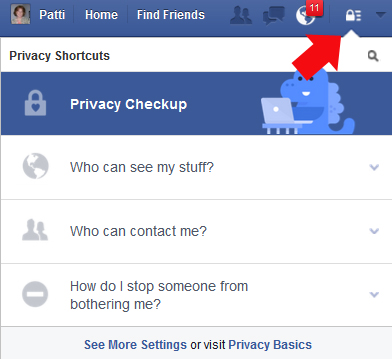
The screens to update your information look like example screens, but they’re actually interactive so you can click and adjust your information.
First Step is “Your Posts”. Remember, Facebook Terms of Service allow that your intellectual property rights (pictures, videos, etc.) are “subject to your privacy and application settings”. So if you set your privacy to “public”, Facebook assumes you mean anyone and everyone.
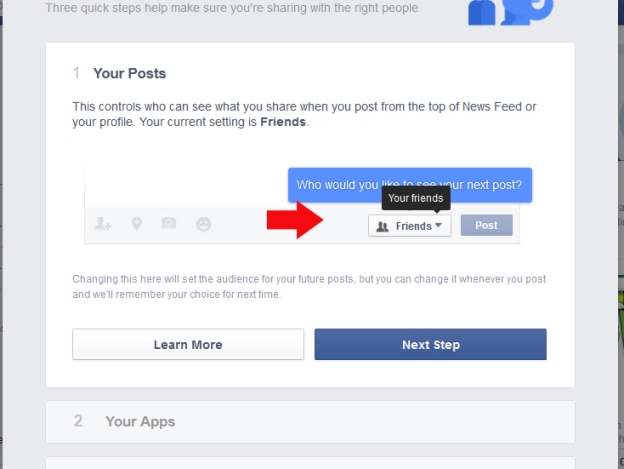
Second Step is setting “Your Apps”. These are sites you’ve logged onto with Facebook. Remember being asked by a website if you want to use Facebook to log on? This is where the sites you said yes to are listed.

FYI: Being a paranoid individual, I rarely sign on with Facebook. Exceptions would be benign website like National Geographic, Washington Post, Fox News, etc. I’m okay with these sites knowing as much about me as Facebook.
Third Step is “Your Profile”. You can make this as secure or as public as you wish. I bet you didn’t know you had an individual Facebook email address, did you? Now you do.
Twitter Privacy
Adjusting Twitter privacy settings are pretty much like any standard website. You can tell people as much or as little as you’d like by what’s in your profile.
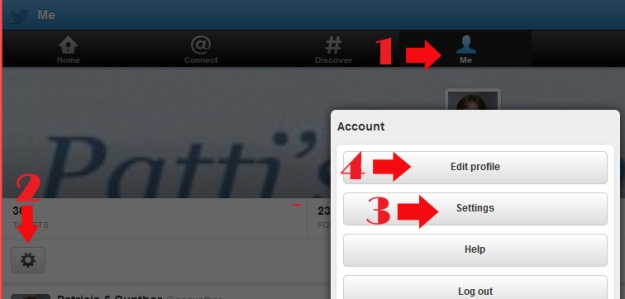
1) Go to the Me tab, 2) left-click the Account gear, then 3) Settings. Under Settings you will see how your information is presented on Twitter. 4) Edit profile will allow you to edit your information.
Pinterest Privacy
PInterest’s privacy settings are accessed in the upper right corner under your name. 1) Left-click the gear, then 2) left-click Account Settings. You don’t need to click “Edit Profile” because you can adjust that under Account Settings.
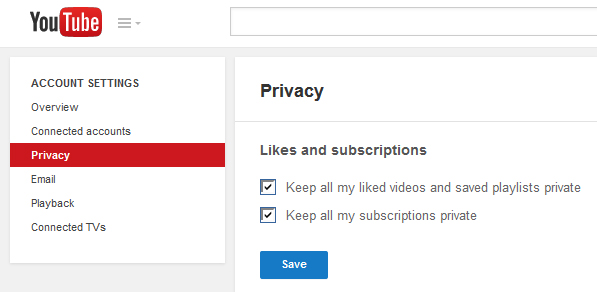
Youtube Privacy
Settings are in the top right corner by your picture. See a pattern here? Many, if not all, setting options are in the upper right corner of your browser window very close to where your picture is or would be if you uploaded one.
1) Left-click your picture, 2) left-click the Settings gear icon,

3) The left margin contains areas you might wish to adjust.
Google+ Privacy
If you don’t know what Google+ is you might not have an accoun t. But, if you have Gmail for your email provider, you might have an account and don’t know it. To find it, in the top right of your email main page you’ll see your name with a + behind it. Left-click on that to get into Google+.
t. But, if you have Gmail for your email provider, you might have an account and don’t know it. To find it, in the top right of your email main page you’ll see your name with a + behind it. Left-click on that to get into Google+.
Google+ Privacy settings are…you guessed it, upper right corner by your picture.
1) Left-click the menu arrow beside the picture area, 2) click Privacy.
If you hover over the Home area to the left, you’ll get more options. You can edit your profile here and access Settings at the bottom of the list.
Don’t forget to update the Audence tab (1). This lets you determine who can see your Google+ stuff. It’s under Settings.
I hope you now know a bit more about how much of yourpersonal information is accessable through websites.
There is great government website that addresses these issues also: Guide to Keeping Your Social Media Accounts Secure 2015 .
Rest easy with your new social media piece of mind, and thanks again for following Patti’s Pathways. 😀
Other security articles you might find interesting:
Facebook: LIttle Known Tips and Tricks Tip Six three-fourths of the way down the page also talks about public posts on Facebook.
Giving Out Credit Card Numbers
Microsoft Won’t Call You…EVER!
DISCLAIMER: Any and all ideas presented in this blog are solely my own. I experience troubles with technology just like any other person, and if I stumble upon a fix or suggestion I feel could benefit others I pass it along. At no time, have I suggested or implied that I hold any degrees or certificates related to computer repair.
I have during my career assembled parts into working computers; done troubleshooting on hardware and software; utilized a great many computer programs and software; designed and updated websites and blogs; as well as created brochures, banners, and flyers.










