This post was originally going to be “How to Permission Protect Your Windows 8 Folders” because chatter on the web said there is no way to password-protect folders in Windows 8.
 Surprise! You can password protect folders in Windows 8. You do this by using a zip program and archiving your special folder. After doing a bunch of dancing around, you’ll get password protected folders and files.
Surprise! You can password protect folders in Windows 8. You do this by using a zip program and archiving your special folder. After doing a bunch of dancing around, you’ll get password protected folders and files.
Be forewarned. The choreography sounds complicated, but you’re a good dancer so I think you can follow.
Now… get ready to dance. I’m leading.
Dance Step One:
Create a Restore Point.
In Windows 8 and 8.1 to create a restore point go to Control Panel > Recovery > Configure System Restore. Don’t forget there’s always an uninstall option at Control Panel > Programs if you don’t like a program.
Dance Step Two:
Find a good file archive program. I have WinZip, but the free archiver I tested for my faithful readers is 7-Zip.
What’s a file archive program? A file archiver either 1) compresses information to take up less hard drive or download space, or 2) makes files and folders easier to send between people since they are archived with file content and not a specific file system.
MORE THAN YOU EVER WANTED TO KNOW ABOUT FILE SYSTEMS: Different digital devices use different file systems to store data. Flash drive content is stored differently than CDs/DVDs. Different operating systems also have different file system types. Microsoft/Windows file system (usually FAT or NTFS) is different from the Macintosh/Apple file system (HFS). For the pre-computer crowd, think Dewey Decimal System versus strict alphabetical order.
Now to toss a watusi step into a rumba dance to confuse you further. File systems are not the same as file extensions (.exe, .doc, .jpg, .zip, .bat, .epub).
Why did I choose 7-Zip to test? Out of 5 stars, it still has a 4- to 4 1/2-star approval rating from users after 8 million downloads at cnet.com. Cnet editors gave the 32-bit a 5-star rating, but didn’t rerate the 64-bit program. I’m using 64-bit with no troubles.
Psst! If you’ve been following this blog, you’ve figured out my favorite program download site is cnet (download.com). I’ve used it for years and have never gotten a virus, plus little or no adware sneaks in with your downloads.
HEADS UP: On download.com — and a lot of other download sites — don’t be confused by paid advertisers on the same page as program downloads. Paid advertiser download buttons are in a box usually with the name of the paid program beside the button.
In the above example, the top free download is RegClean Pro. The name’s fairly well hidden, but you can find it if you try. The second impersonator for our download is Bitdefender. I’m sure it’s a very nice program, but we don’t want it today. We want 7-Zip.
7-Zip
http://download.cnet.com/7-Zip/3000-2250_4-10045185.html
7-Zip 64-bit
http://download.cnet.com/7-Zip-64-bit/3000-2250_4-10905593.html
After downloading 7-Zip, follow the prompts to install.
Oh good, the band is back to playing our waltz.
How To Password Protect Items in Windows 8
1) Find the folder you wish to password protect.
For demonstration purposes, I made a TEST  folder on my desktop. I’d suggest you do the same until you are familiar with how this works. Toss a test.doc or two into your TEST folder. You’ll need something to protect or it doesn’t work. At least, it didn’t for me.
folder on my desktop. I’d suggest you do the same until you are familiar with how this works. Toss a test.doc or two into your TEST folder. You’ll need something to protect or it doesn’t work. At least, it didn’t for me.
Note on Photos and Clipart: .jpg, .gif, .png, and others save in zip archives, but don’t open. Some premium archiver programs have an image viewer capability. If you don’t have one of those, you can unzip/move the photo to a regular unarchived file/folder to view.
2) Right-click your TEST folder, 3) choose 7-Zip, then 4) Add to archive…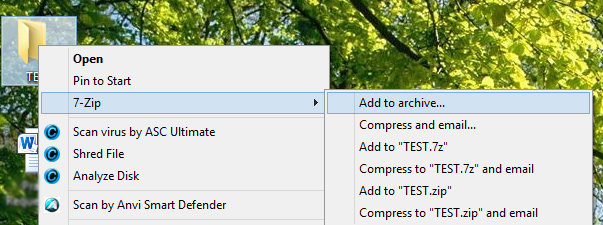
5) Make sure the Archive Format is zip, and the Encryption method is ZipCrypto. This allows someone you’ve given the password to the ability to open this file with any zip program. 6) Enter a password of 8 digits, and 7) Press OK.
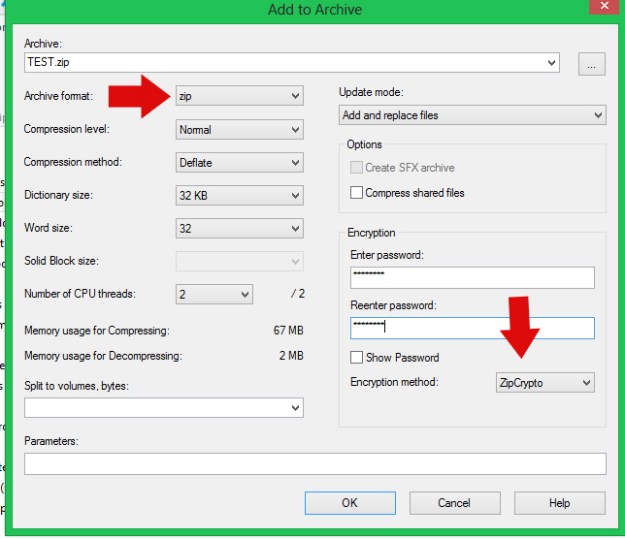
8) Locate the .zip folder you’ve just created.
The easiest way is clicking the  folder icon on your task bar, then under Desktop find your TEST folder. You can also use Windows key + X, and search for your .zip folder with the File Explorer.
folder icon on your task bar, then under Desktop find your TEST folder. You can also use Windows key + X, and search for your .zip folder with the File Explorer.
Your original TEST folder is still there. That’s the one you made first, but not the archived one. To find the archived one, scroll down a little farther. If you see a TEST.7z folder, you archived your folder in 7-Zip format.
Did you notice my archived folders show as WinZip files? That’s because WinZip is my default archive program. My new password protected files open in WinZip also.
9) Left-click on your TEST.zip folder and you’ll get a prompt to enter a password. That’s the password you just assigned in 7-Zip: Add to Archive. 10) Enter your password.

10) Choose the document in the folder you wish to open/edit. Now you’re free to edit the item as you wish.
FYI: If you don’t close the archived folder, you shouldn’t need to reenter the password to access other documents in that folder.
A WORD ON SAVING YOUR FOLDER:
When you exit your new .zip folder, 7-Zip is so nice, it’ll ask if you want to update it. You do.

WINZIP NOTE: If you’re default program is WinZip, you’ll get this save screen.
 You want the top option. WinZip now asks for another password. It must think an updated document needs an updated password. I use the original pass I set. If you don’t edit the file, WinZip doesn’t ask to update the password.
You want the top option. WinZip now asks for another password. It must think an updated document needs an updated password. I use the original pass I set. If you don’t edit the file, WinZip doesn’t ask to update the password.
There. You’re done! You’ve created a new password protected .zip folder, and you’re free to delete your original folder.
I played around for a while before actually deleting any folders. My password protected folders are still working. All seems right in the .zip computing world.
Are there any downsides?
The only downside I see is adding items to your protected .zip folder.
Creating new folders in either 7-Zip or WinZip is easy. Right-click in the protected folder body (or chose the File command at the top bar), then left-click “New Folder” or “Create Folder”.
The tricky step is adding documents or photos within a protected folder in 7-Zip.
Archive programs are made to conserve space or make data more portable, not as a place to create documents, view photos, et cetera.
7-Zip:
Let’s talk about adding items in 7-Zip first.
I will requote the old adage: You get what you pay for. This free program makes it necessary to dance around again to add items.
7-Zip does have a “Create File” option, but for some reason, it doesn’t work for me nor can I find anyone on the forums who succeeded with it. Let me know if it works for you.
To add photos or documents using 7-Zip, they need to be 1) archived first (a new .zip made), then 2) dragged and dropped into your password protected archived folder. Cut and paste aren’t supported.
It might be of greater benefit in 7-Zip to resave old items from your protected folder in a new regular folder with the new items you want to password protect, then rearchive them all.
Why? Each added item equals a new folder. Soon, if you have a lot of super secret stuff, you’ll have oodles of folders to waltz through to find the one you want.
WINZIP:
Adding photos or documents using WinZip is much easier. 1) Create and save your item as usual. 2) Drag and drop it into your password protected Winzip folder. 3) With the document name highlighted, 4) open Tools, and 5) choose Encrypt Zip File.
When it asks a password, continue with the steps you used before to edit and save it. When you close your newly added file, WinZip will password protect it.
I know this is a lot to process, but if you wish to password protect your data in Windows 8, you must learn the tough routines. And pray Windows 9 allows password protecting files again then upgrade.
You should pat yourself on the back though.  You’re a great dance partner. Now sit this next set out and put your feet up, you’ve worked hard.
You’re a great dance partner. Now sit this next set out and put your feet up, you’ve worked hard.
Have a productive week, and thanks again for following Patti’s Pathways. 😀
Other posts that compliment this one:
On The Threshhold of Windows 9
DISCLAIMER: Any and all ideas presented in this blog are solely my own unless otherwise noted. I experience troubles with technology just like any other person, and if I stumble upon a fix or suggestion I feel could benefit others I pass it along. At no time, have I suggested or implied that I hold any degrees or certificates related to computer repair.
I have during my career assembled parts into working computers; done troubleshooting on hardware and software; utilized a great many computer programs and software; designed and updated websites and blogs; as well as created brochures, banners, and flyers.
































 I’ve had requests to blog about useful Gmail tips and tricks. There are enough I could string this out over weeks. I won’t.
I’ve had requests to blog about useful Gmail tips and tricks. There are enough I could string this out over weeks. I won’t.

 FYI: If Contacts won’t open — there’s a perpetual message of Loading… -or- Still Working… — clear your browser history and/or cookies.
FYI: If Contacts won’t open — there’s a perpetual message of Loading… -or- Still Working… — clear your browser history and/or cookies.























 to me via Dropbox.
to me via Dropbox. rifling through my confidential files. I bank online, I dabble in the stock market online, and more.
rifling through my confidential files. I bank online, I dabble in the stock market online, and more.
 technology advice from a woman who has no keypad on her phone?
technology advice from a woman who has no keypad on her phone?



 programming problem many of us were experiencing, but no one was detailing a fix. My blog received thousands of hits in a short time. I like writing so I wanted to expand my blog, but I also wanted a more professional URL.
programming problem many of us were experiencing, but no one was detailing a fix. My blog received thousands of hits in a short time. I like writing so I wanted to expand my blog, but I also wanted a more professional URL. The Save Draft button is your best friend, while the Preview button is everyone else’s best friend. Preview allows you — and only you — to review your raw post before publication without forcing the general populace to do the same. Using Preview only, you can make a test blog in perpetual draft format to play with in your blog editing program.
The Save Draft button is your best friend, while the Preview button is everyone else’s best friend. Preview allows you — and only you — to review your raw post before publication without forcing the general populace to do the same. Using Preview only, you can make a test blog in perpetual draft format to play with in your blog editing program.

 pen your command prompt by holding down the Windows key and pressing “X”.
pen your command prompt by holding down the Windows key and pressing “X”.



